Malicious Email
Cyber-attacks have become increasingly sophisticated and difficult to detect, and malicious email is one of the most common forms of attack. Better known as spam, Memorial University is receiving more and more of these emails every day. In the past year, the daily average number of emails received at the St. John’s campus has tripled to about 2.7 million. While more than 90 percent of these incoming email are blocked each day, some still get through – and everyone must do their part to protect themselves and the University.
By clicking on a phony link in an email or opening an attachment, you may unknowingly put yourself and Memorial at risk. Malicious emails appear to come from legitimate sources. These malicious emails include fake invoices requesting payment, notices that your email quota has been exceeded, or warnings that your account has been accessed with a request to log in to verify your account. Cyber-attackers try to gain access to both your personal and University information by getting you to click on phony links. They also try to get you to open attachments filled with viruses that can infect and damage your computer, or ransomware that locks your files until you pay to get them back.
How to detect a malicious email
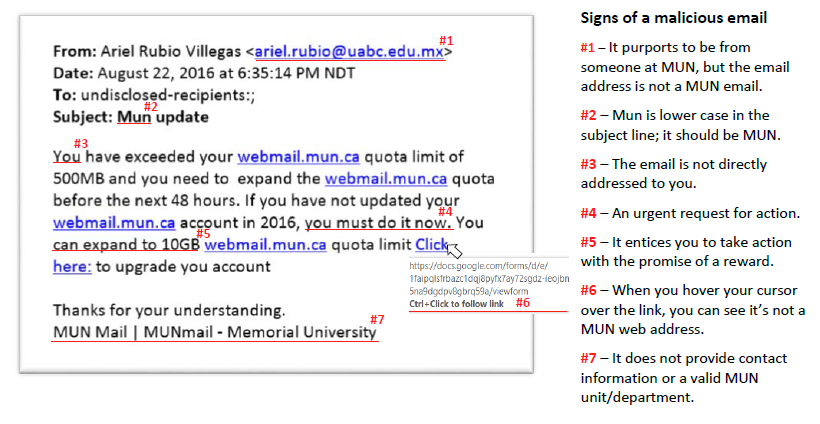
Here’s an example of a phishing email received by some Memorial email users. There are seven signs that this is not a legitimate email:
What you can do to protect yourself
If something seems suspicious or does not feel right, it may be a cyber-attack.
Additional advice includes:
- Never click on web links or attachments in emails from unknown sources
- Never disclose your username and password. Look for signs to identify potentially malicious emails, including:Requests for payment
- Requests for your username and password
- Hover your cursor over the web link to see if the website address is different than what appears in the body of the email
- Slight variations, such as transposed letters, in the email address or website address
- Spelling errors in the email
- Unusual greetings
- Requests for a quick response
- Use your Memorial email account for University business only and use a separate email account for personal matters, such as online shopping, banking, or sending and receiving jokes.
- Keeping business and personal emails separate increases your chances of being able to identify what you should and shouldn’t be receiving in each of your email accounts.
- Back up your files properly. If your backup drive is connected to your computer, it can also be affected by malware. If you need a managed backup service submit a ticket to ECS Service Desk at https://ecs.assist.com/
- If you receive a suspicious email it should be sent, as an attachment, to abuse@mun.ca. With the questionable message highlighted, go to More>Forward as Attachment. If you are using Outlook on the web, start a new email then drag and drop the suspicious message in to the new email.
- Do not forward the message to others as a warning; this expands the number of email accounts that could potentially be affected.